Features
Why TRUSEC?
Contact Us
Ask Anything
Cyber Security
Your AI-powered cybersecurity assistant for threat intelligence, compliance, and security insights.
Contact Us
Ask your Questions
“A specialized security research engine that delivers evidence-cited, up-to-date, expert-level answers across vulnerabilities, threats, techniques, and defenses.”
10x
Faster triage
30-50%
Time saved on research
Ask a question
What You Can Ask TruSec?
From secure coding to threat analysis, TruSec provides expert answers across three key security domains.

Threat Intelligence
"Is this IP address malicious: 192.0.2.1?"
Check against 50+ threat intelligence feeds with reputation scores, associated malware, and historical data.
"Tell me about the Emotet malware family"
Get comprehensive analysis including TTPs, IOCs, distribution methods, and defensive measures.
“What is ransomware and how does it work?"
Understand attack chains, common families, prevention strategies, and incident response procedures.

Application Security
"What is SQL injection and how do I prevent it?"
Get detailed explanations of attack vectors, code examples in multiple languages, and OWASP recommendations.
"Explain the OWASP Top 10 vulnerabilities"
Understand each vulnerability with real-world examples and mitigation strategies.
"How do I implement secure password hashing?"
Learn about bcrypt, Argon2, and best practices for password storage with code samples.

Compliance & Regulations
"What is SQL injection and how do I prevent it?"
Get detailed explanations of attack vectors, code examples in multiple languages, and OWASP recommendations.
"Explain the OWASP Top 10 vulnerabilities"
Understand each vulnerability with real-world examples and mitigation strategies.
"How do I implement secure password hashing?"
Learn about bcrypt, Argon2, and best practices for password storage with code samples.
Specs
Why Choose Trusec?
TruSec reasons like a security analyst. TruSec is trained and optimized exclusively for security workflows.
Feature
Security Expertise
Data & Training
Freshness
Speed
Context Awareness
Usability
Purpose-built for cybersecurity with deep domain context
Trained on security-specific data
Real-time threat intelligence from 50+ sources
Instant, comprehensive answers
Conversational, remembers context and follow-ups
Ask, refine, and explore naturally
Generic AI Search
Generic results across all topics
Broad web indexing
Outdated blogs and SEO-ranked content
Manual scanning across multiple links
Each search starts from scratch
Repeated keyword searches
Knowledge Source
Security-Specific Reasoning Engine
Access real-time threat data from over 50 trusted sources. TruSec aggregates and correlates intelligence to provide actionable insights for your security operations.
01
Real-time Updates: Continuous synchronization with threat intelligence feeds
02
Contextual Analysis: AI-powered correlation across multiple threat sources
03
Custom Integration: Add your organization-specific threat intelligence feeds
Threat & Malware Intelligence
ThreatFox - Malware IOCs (IPs, domains, file hashes)
URLhaus - Verified malicious URLs
ThreatFox - MalwareBazaar – Malware samples and hash intelligence
SSL Blacklist – Malicious SSL certificate tracking
Spamhaus DROP List – High-risk IPs and domains linked to spam and abuse
Detection & Correlation Intelligence
Sigma & YARA Rules – Detection logic for log and file scanning
AlienVault OTX – Community-driven threat pulses
MISP Taxonomies & Galaxies – Structured threat classification and context
Threat & Malware Intelligence
MITRE CWE - Standardized vulnerability taxonomy
URLhaus - Verified malicious URLs
CISA KEV – Known exploited vulnerabilities in the wild
MITRE ATT&CK (TAXII / STIX) – Adversary tactics, techniques, and procedures
Features
Powerful Features for Modern Security Teams
From threat intelligence to automated response, TruSec provides everything you need to stay ahead of cyber threats.
Intelligent Chat Interface
Chat UI with conversation history, suggested follow-ups, and natural language queries for threat investigation.
Actionable Guidance
Deliver accurate security insights, step-by-step implementation guidance, risk mitigation strategies, and up-to-date threat intelligence.
Deep Threat Investigation
Analyze IOCs, investigate threats and malware, perform forensic analysis, and correlate security events to uncover attack patterns.
Security Knowledge & Best Practices
SOAR Capabilities
Execute automated response actions with human-in-the-loop approval mechanisms and status updates back to your SIEM/JIRA tickets.

Coming Soon
Seamlessly Integrate






Get professional-grade, security researched answers!
Join SOC analysts, AppSec engineers, and security teams who trust TruSec for fast, accurate, evidence-cited security intelligence.
info@trusys.ai
Features
Why TRUSEC?
Contact Us
Ask Anything
Cyber Security
Your AI-powered cybersecurity assistant for threat intelligence, compliance, and security insights.
Contact Us
Ask your Questions
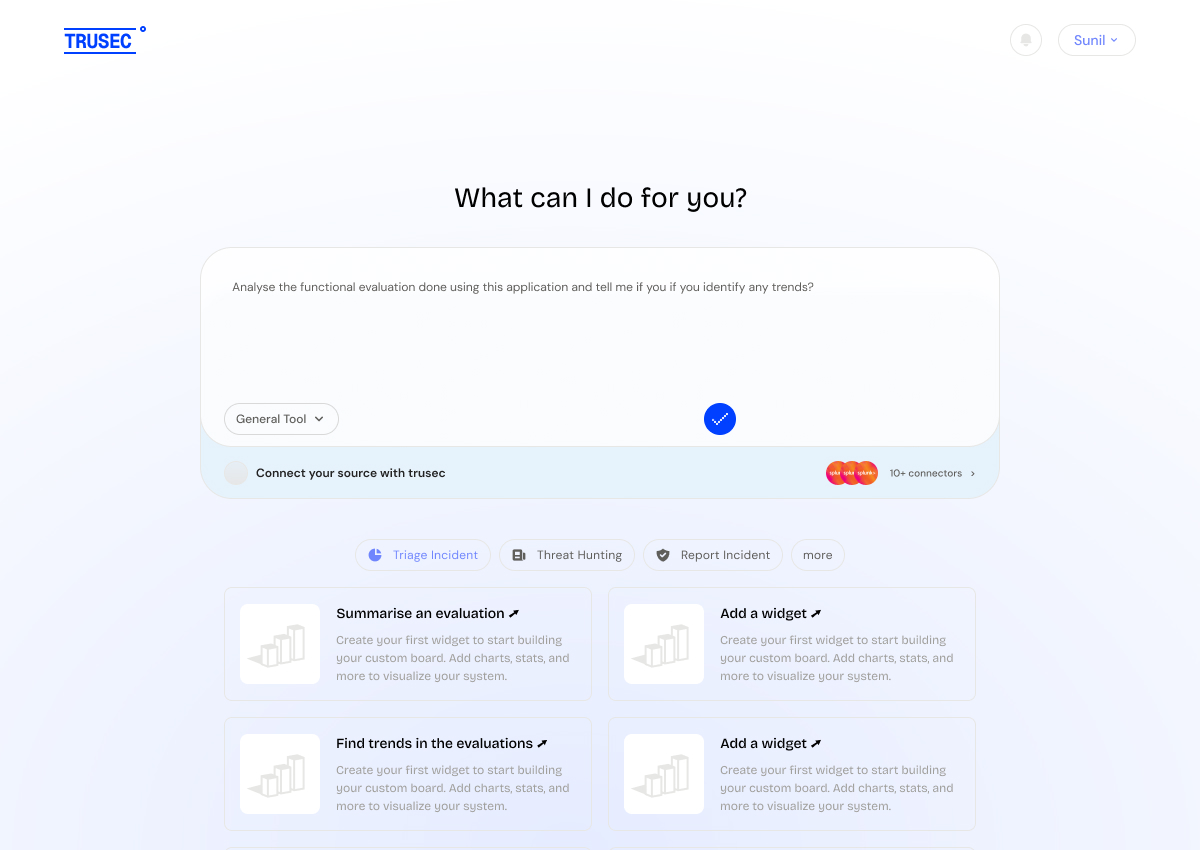
“A specialized security research engine that delivers evidence-cited, up-to-date, expert-level answers across vulnerabilities, threats, techniques, and defenses.”
10x
Faster triage
30-50%
Time saved on research
Ask a question
What You Can Ask TruSec?
From secure coding to threat analysis, TruSec provides expert answers across three key security domains.

Threat Intelligence
"Is this IP address malicious: 192.0.2.1?"
Check against 50+ threat intelligence feeds with reputation scores, associated malware, and historical data.
"Tell me about the Emotet malware family"
Get comprehensive analysis including TTPs, IOCs, distribution methods, and defensive measures.
“What is ransomware and how does it work?"
Understand attack chains, common families, prevention strategies, and incident response procedures.

Application Security
"What is SQL injection and how do I prevent it?"
Get detailed explanations of attack vectors, code examples in multiple languages, and OWASP recommendations.
"Explain the OWASP Top 10 vulnerabilities"
Understand each vulnerability with real-world examples and mitigation strategies.
"How do I implement secure password hashing?"
Learn about bcrypt, Argon2, and best practices for password storage with code samples.

Compliance & Regulations
"What is SQL injection and how do I prevent it?"
Get detailed explanations of attack vectors, code examples in multiple languages, and OWASP recommendations.
"Explain the OWASP Top 10 vulnerabilities"
Understand each vulnerability with real-world examples and mitigation strategies.
"How do I implement secure password hashing?"
Learn about bcrypt, Argon2, and best practices for password storage with code samples.
Specs
Why Choose Trusec?
TruSec reasons like a security analyst. TruSec is trained and optimized exclusively for security workflows.
Feature
Security Expertise
Data & Training
Freshness
Speed
Context Awareness
Usability
Purpose-built for cybersecurity with deep domain context
Trained on security-specific data
Real-time threat intelligence from 50+ sources
Instant, comprehensive answers
Conversational, remembers context and follow-ups
Ask, refine, and explore naturally
Generic AI Search
Generic results across all topics
Broad web indexing
Outdated blogs and SEO-ranked content
Manual scanning across multiple links
Each search starts from scratch
Repeated keyword searches
Knowledge Source
Security-Specific Reasoning Engine
Access real-time threat data from over 50 trusted sources. TruSec aggregates and correlates intelligence to provide actionable insights for your security operations.
01
Real-time Updates: Continuous synchronization with threat intelligence feeds
02
Contextual Analysis: AI-powered correlation across multiple threat sources
03
Custom Integration: Add your organization-specific threat intelligence feeds
Threat & Malware Intelligence
ThreatFox - Malware IOCs (IPs, domains, file hashes)
URLhaus - Verified malicious URLs
ThreatFox - MalwareBazaar – Malware samples and hash intelligence
SSL Blacklist – Malicious SSL certificate tracking
Spamhaus DROP List – High-risk IPs and domains linked to spam and abuse
Detection & Correlation Intelligence
Sigma & YARA Rules – Detection logic for log and file scanning
AlienVault OTX – Community-driven threat pulses
MISP Taxonomies & Galaxies – Structured threat classification and context
Threat & Malware Intelligence
MITRE CWE - Standardized vulnerability taxonomy
URLhaus - Verified malicious URLs
CISA KEV – Known exploited vulnerabilities in the wild
MITRE ATT&CK (TAXII / STIX) – Adversary tactics, techniques, and procedures
Features
Powerful Features for Modern Security Teams
From threat intelligence to automated response, TruSec provides everything you need to stay ahead of cyber threats.
Intelligent Chat Interface
Chat UI with conversation history, suggested follow-ups, and natural language queries for threat investigation.
Security Knowledge & Best Practices
SOAR Capabilities
Execute automated response actions with human-in-the-loop approval mechanisms and status updates back to your SIEM/JIRA tickets.
Actionable Guidance
Deliver accurate security insights, step-by-step implementation guidance, risk mitigation strategies, and up-to-date threat intelligence.
Deep Threat Investigation
Analyze IOCs, investigate threats and malware, perform forensic analysis, and correlate security events to uncover attack patterns.

Coming Soon
Seamlessly Integrate






Get professional-grade, security researched answers!
Join SOC analysts, AppSec engineers, and security teams who trust TruSec for fast, accurate, evidence-cited security intelligence.
info@trusys.ai
Features
Why TRUSEC?
Contact Us
Ask Anything
Cyber Security
Your AI-powered cybersecurity assistant for threat intelligence, compliance, and security insights.
Contact Us
Ask your Questions

“A specialized security research engine that delivers evidence-cited, up-to-date, expert-level answers across vulnerabilities, threats, techniques, and defenses.”
10x
Faster triage
30-50%
Time saved on research
Ask a question
What You Can Ask TruSec?
From secure coding to threat analysis, TruSec provides expert answers across three key security domains.

Threat Intelligence
"Is this IP address malicious: 192.0.2.1?"
Check against 50+ threat intelligence feeds with reputation scores, associated malware, and historical data.
"Tell me about the Emotet malware family"
Get comprehensive analysis including TTPs, IOCs, distribution methods, and defensive measures.
“What is ransomware and how does it work?"
Understand attack chains, common families, prevention strategies, and incident response procedures.

Application Security
"What is SQL injection and how do I prevent it?"
Get detailed explanations of attack vectors, code examples in multiple languages, and OWASP recommendations.
"Explain the OWASP Top 10 vulnerabilities"
Understand each vulnerability with real-world examples and mitigation strategies.
"How do I implement secure password hashing?"
Learn about bcrypt, Argon2, and best practices for password storage with code samples.

Compliance & Regulations
"What is SQL injection and how do I prevent it?"
Get detailed explanations of attack vectors, code examples in multiple languages, and OWASP recommendations.
"Explain the OWASP Top 10 vulnerabilities"
Understand each vulnerability with real-world examples and mitigation strategies.
"How do I implement secure password hashing?"
Learn about bcrypt, Argon2, and best practices for password storage with code samples.
Specs
Why Choose Trusec?
TruSec reasons like a security analyst. TruSec is trained and optimized exclusively for security workflows.
Feature
Security Expertise
Data & Training
Freshness
Speed
Context Awareness
Usability
Purpose-built for cybersecurity with deep domain context
Trained on security-specific data
Real-time threat intelligence from 50+ sources
Instant, comprehensive answers
Conversational, remembers context and follow-ups
Ask, refine, and explore naturally
Generic AI Search
Generic results across all topics
Broad web indexing
Outdated blogs and SEO-ranked content
Manual scanning across multiple links
Each search starts from scratch
Repeated keyword searches
Knowledge Source
Security-Specific Reasoning Engine
Access real-time threat data from over 50 trusted sources. TruSec aggregates and correlates intelligence to provide actionable insights for your security operations.
01
Real-time Updates: Continuous synchronization with threat intelligence feeds
02
Contextual Analysis: AI-powered correlation across multiple threat sources
03
Custom Integration: Add your organization-specific threat intelligence feeds
Threat & Malware Intelligence
ThreatFox - Malware IOCs (IPs, domains, file hashes)
URLhaus - Verified malicious URLs
MalwareBazaar – Malware samples and hash intelligence
SSL Blacklist – Malicious SSL certificate tracking
Spamhaus DROP List – High-risk IPs and domains linked to spam and abuse
Detection & Correlation Intelligence
Sigma & YARA Rules – Detection logic for log and file scanning
AlienVault OTX – Community-driven threat pulses
MISP Taxonomies & Galaxies – Structured threat classification and context
Threat & Malware Intelligence
MITRE CWE - Standardized vulnerability taxonomy
URLhaus - Verified malicious URLs
CISA KEV – Known exploited vulnerabilities in the wild
MITRE ATT&CK (TAXII / STIX) – Adversary tactics, techniques, and procedures
Features
Powerful Features for Modern Security Teams
From threat intelligence to automated response, TruSec provides everything you need to stay ahead of cyber threats.
Intelligent Chat Interface
Chat UI with conversation history, suggested follow-ups, and natural language queries for threat investigation.
Security Knowledge & Best Practices
Explain security standards, guide policies and compliance, cover cloud, application, and infrastructure security, and highlight emerging threats.
Actionable Guidance
Deliver accurate security insights, step-by-step implementation guidance, risk mitigation strategies, and up-to-date threat intelligence.
Deep Threat Investigation
Analyze IOCs, investigate threats and malware, perform forensic analysis, and correlate security events to uncover attack patterns.

Coming Soon
Seamlessly Integrate






Get professional-grade, security researched answers!
Join SOC analysts, AppSec engineers, and security teams who trust TruSec for fast, accurate, evidence-cited security intelligence.